KX Technical and Organizational Measures
The Technical and Organizational Measures (TOMs) provided below applies to the KX business. Evidence of the measures implemented and maintained by KX may be provided in the form of up-to-date compliance attestations upon request from the customer.
The TOMs are assessed annually through both internal testing and formal audit. A formal Senior Management Review is held biannually to assess and evaluate the effectiveness of our Information Security Management System (ISMS).
Security Policies
KX maintains a robust Information Security Management System (ISMS). Security policies are reviewed annually and amended as necessary to maintain security compliance.
A formal Management Review is held every 6 months to assess and evaluate the effectiveness of technical and organizational measures. This includes tracking metrics related to the Governance, Risk and Compliance of our Information Security Management System.
KX employees complete Security and Privacy training annually. KX has an Information Security and Compliance Organization structure which oversees all Information Security related policies, programs and activities for KX.
- KX has defined and documented data privacy policies and processes addressing access to personal data.
- Mandatory Information Security awareness training is provided.
- KX continuously reviews event logs for malicious/abnormal behavior.
- All confirmed incidents reported are analyzed for root cause and impact. The remedial actions are initiated by the process owners. The key incidents along with their root causes and impact are reported to KX management.
Internal IT and IT Security Governance and Management
A formal Internal Audit program is operated to measure the conformance and governance of our ISMS controls. Metrics from our Internal Audit program are presented at our Management Reviews.
Certification and Assurance of Process and Products
External, independent audits are organized and managed to meet our business needs with respect to certification and assurance. This includes a full and formal examination of the process, products and functions that are supported by our ISMS.
Risk Management
KX has defined, documented, and implemented a Risk Management framework based on ISO 27005 to identify risks related to security, privacy and other contractual requirements. All risks are evaluated to determine their impact to the business, and then assessed to determine the correct treatment action.
KX assesses, addresses risks, and creates action plans to mitigate identified risks. All risks are reviewed as needed, once a year at a minimum.
Incident Management – KX Business
KX maintains a company level incident response policy and follows documented incident response plans including prompt breach notifications as appropriate, to the relevant authorities, customers, and data subjects when a breach is known or reasonably suspected to impact customer data stored in KX systems.
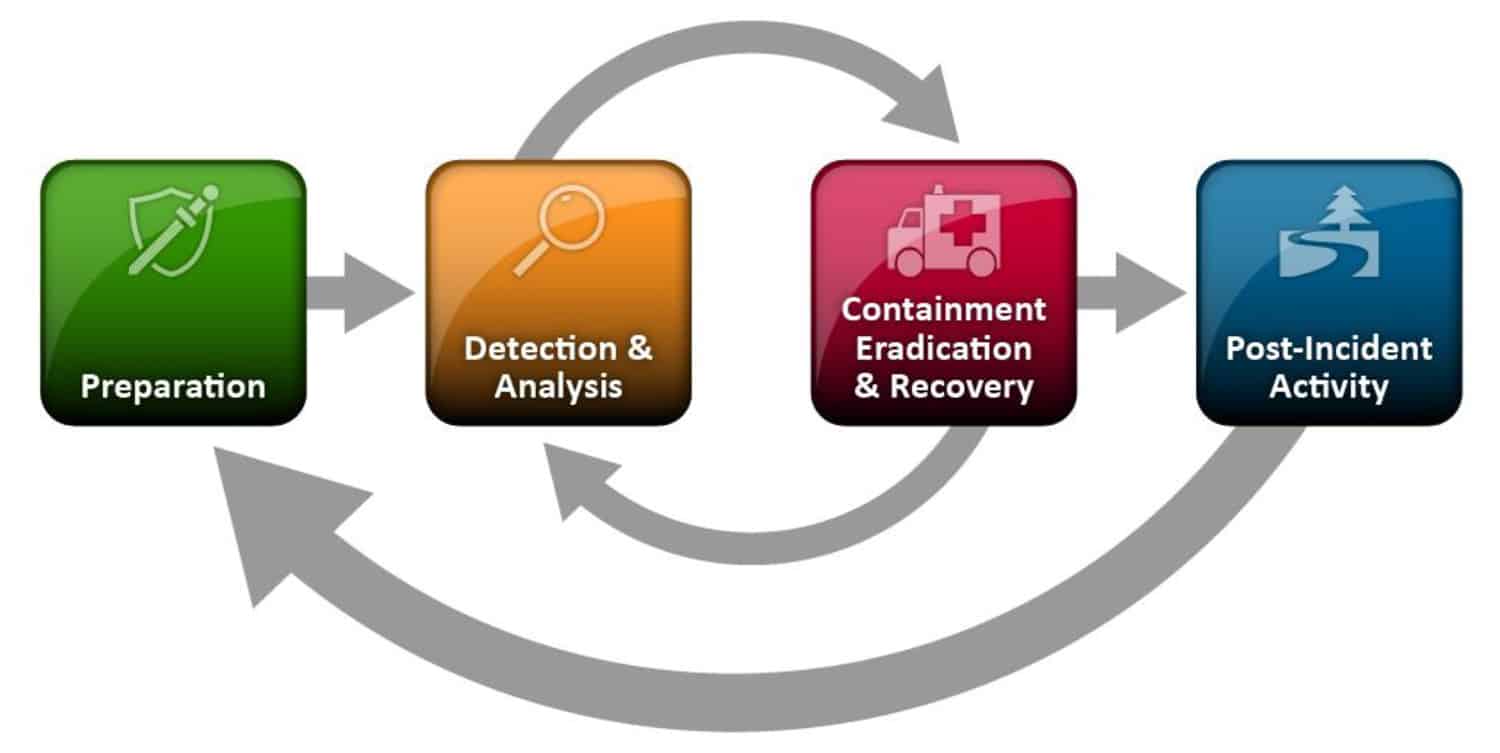
The KX Incident Response program follows NIST 800-61 r2 (see diagram below)
KX maintains separate flows for the following incidents:
- Cybersecurity incidents
- Data incidents (including Privacy team when personal data is impacted)
Communication outside of KX is handled by the appropriate customer-facing resources.
KX monitors for security incidents 24×7 and escalates to the appropriate Incident Management Response team when an event is detected. The incident process includes isolation/eradication/retention as required, and a root cause analysis is performed for high/critical incidents. Post-incident activity also includes reviews to improve processes/tools as needed.
Data Privacy
KX maintains a privacy program that is designed to comply with all privacy regulations applicable to the company and the personal data we hold. We have processes in place to ensure that we handle the personal data of our customers in accordance with our legal obligations and our customer contracts. The privacy program includes, among other things, the following:
- Data protection impact assessment
- Policies and Procedures
- Privacy Employee Awareness Training
- Data Processing Terms
- Data Transfer Mechanisms
- Response to Data Subject Requests
- Incident Response
- Documenting Compliance with Global Privacy Regulations
KX Use of Sub-Processors
https://kx.com/legal/kx-insights-platform-subprocessors/
How KX Support Protects Your Data
Ensuring Data Minimization
The KX Support Organization collects only that personal data which is shared with them by the client for the purposes of providing support and related services to our customers.
Encryption of Personal Data
KX protects client data through encryption.
- When personal data is transmitted to or from KX, secure end-to-end encryption of the communication is ensured.
- Data in Transit – TLS (Transport Layer Security) encryption is required for all Internet connections during login and all data shall be encrypted during transmission. All personal data transfers occur over HTTPS/SFTP and use minimum TLS 1.2 protocol.
- Data at Rest – Stored customer data is encrypted at rest using AES-256 encryption. Key Management conforms to industry best practices.
Measures of Encryption
Encryption Key Management – Cryptographic key management procedures are documented. Products or solutions are deployed to keep the data encryption keys encrypted (e.g., software- based solution, Hardware Security Module (HSM)). This is software-based Encryption, Key Management procedure will be automated. Encryption of data is configured at rest and in transit.
Encryption Uses – Confidential information transmission over the public internet always utilizes an encrypted channel. Encryption details are documented if transmission is automated. If manual encryption is required, approved, and dedicated staff is responsible for encrypting / decrypting the data. Confidential information is encrypted while in transit over any network using secure protocols like HTTPS, SSL, SFTP, etc. VPN transmissions are performed over an encrypted channel.
Confidentiality, Integrity, Availability and Resilience of Processing Systems
The KX Support Organization ensures that appropriate controls are in place to safeguard the confidentiality, integrity, and accessibility of KX Support systems and customer data.
- KX has a process for onboarding and offboarding of users to prevent unauthorized access to data.
- Roles and Responsibilities are implemented within the Support Organization to reduce opportunities for unauthorized or unintentional modification or misuse of data.
Ability to Restore Availability of, and Access to Client Data
The KX Support Organization is part of the KX Business Continuity Plan in place ensuring the availability of Support services in the event of an outage. The BCP ensures restoration of operations to a pre-defined level, within a predetermined time frame, following a business disruption. The BCP is annually tested.
Database backups are taken with the goal of preventing the loss of personal data in the event of a technical malfunction or human error.
Business Continuity and Disaster Recovery
- Backup procedures are applied to all critical development systems.
- Backup is done at the storage level and industry standards are followed. Each Data Center has its own backup infrastructure. Data storage procedures comply with the ISO 27001 standard.
- Interruptions and outages are communicated to affected customers. Communication includes the following information:
- Nature of impact
- Locations / departments / process impacted
- Extent of impact
- Location and contact information of the IT helpdesk
Asset Management and Associated Controls
- All Assets are formally declared, reviewed and managed on an Asset Register
- Laptops, Desktops, Software, Servers, Network equipment, etc.
- Vendor recommended Operating System patches are tested and applied regularly to the desktops, laptops, servers, and networking equipment.
- Default IDs are changed and disabled. Passwords are changed after initial installation. Manufacturers’ default passwords are not used.
- If sharing of files/directories from a server to other computers is required, it is enabled in such a way that only users who have need to know have access to the share. Principle of least privilege is followed.
- Systems clocks of all the servers and networking equipment are synchronized, and they are set the time zone where the server/equipment are location. Only authorized personnel have the privilege to change or reset system clock time.
- Administrative accounts are set with strong passwords and privileges are given to only identified persons. Admin access is regularly reviewed.
- Endpoint Detection and Response (Antivirus & Malware) software is installed where applicable.
- Backups are taken and restoration checks are done for identified systems.
- Every KX employee requires a unique ‘User ID’ and password to access the IT systems in the enterprise.
- Every user ID has a password and users are required to set and change their passwords as per the KX password policy.
- User IDs are created as per defined process and with adequate authorizations.
- Shared service accounts are managed via Privileged Access Management platform.
User Access Management
KX maintains appropriate controls for requesting, approving, granting, revoking and revalidating user access to systems. Only employees with a business need may access data. Access requests are approved based on an individual’s role and user access is reviewed regularly.
Logical access procedures define the request, approval, access provisioning and de-provisioning processes. The logical access procedures restrict user access (local or remote) based on user job function for applications and databases (role/profile based appropriate access) for applications, databases and systems to ensure segregation of duties. The procedures are reviewed, administered, and documented based on on-boarding, resource re-assignment or separation. User access reviews are performed to ensure access is appropriate throughout the year.
- All KX system administrators are authenticated using multi-factor authentication, VPN, AD for system access through privileged access management.
- The use of privileged access management is recorded for audit and forensic analysis.
User Identification and Authorization
Every user has unique access control (user id and password) to access their accounts.
Cloud Security
Cloud assets, and services are hardened with Center for Internet Security (CIS) Benchmarks.
- Cloud Security Posture Management standards and configurations are monitored in real-time by our DevSecOps Team.
- A Cloud Workload Protection platform is employed within our CSPs (EDR & A/V is installed as standard on end user computing devices, and on a subset of servers)
Security Operations Center
KX has a 24/7 365 SOC Team that provides monitoring and response services for deviations from defined standards, malicious and/or abnormal activity and threat modeling.
- Defined CSIRT Response team.
- Cybersecurity forensics services.
Other Security Controls
- Firewalls are configured in such a way that only authorized layer 7 application traffic is allowed.
- All secured communications at KX follow the current encryption standard.
- EDR is installed on all end user machines.
Wireless Controls
Guest networks are completely segregated with clients issued an IP address by Meraki. All traffic is routed directly to the internet without being able to interact with our corporate networks.
Email Security
- All emails are scanned for virus or malicious codes at gateway level.
- Email systems are configured to restrict identity spoofing, spamming, and relaying to protect against the same.
Physical Security
KX maintains the physical security of its facilities and Data Centers, which includes taking precautions against environmental threats and power disruptions.
- Access to Data Centers is controlled and limited by job role and subject to approval.
- Access to Data Centers is provided on a need only basis and reviewed periodically.
- Physical access to offices is controlled by an access control mechanism.
- Visitor entry is monitored and recorded. (recorded in a log book)
- All critical areas are CCTV covered and recordings are maintained for at least 30 days.
Application Security
At KX, security is integrated into the software development lifecycle (SDLC) process.
- Design: Security implications are considered as part of the application design process. Technical specifications capture security requirements and considerations, and are peer reviewed prior to development beginning.
- Development: Security is embedded in all stages of the development practice. This includes peer code reviews and use of code analysis and vulnerability scanning tools as part of continuous integration.
- Testing: Security testing is performed throughout the development lifecycle. Manual and automated security tests are developed or updated as required. Release Management checklists are used to confirm issues are addressed and security scans are complete.
- Vulnerability Management: Vulnerabilities are reviewed by Development Teams, and assessed and scheduled for patching as part of our release meetings. Vulnerabilities are assigned a severity and resolved via patch release.